Sygnia Discovers New Active China-Nexus Threat Actor Weaver Ant
Sygnia Discovers New Active China-Nexus Threat Actor Weaver Ant
Incident Response leader reveals Weaver Ant leveraged home routers to target top telecoms company and collect sensitive information
TEL-AVIV, Israel & NEW YORK--(BUSINESS WIRE)--Sygnia, the foremost global cyber readiness and response team, revealed today a new China nexus threat actor, which the company has named Weaver Ant. To infiltrate the telecom company and gain access to sensitive data, Weaver Ant compromised Zyxel CPE home routers as an entry point into the victim’s network. The APT also utilized a new web shell, dubbed “INMemory” to enable in-memory execution of malicious modules while evading detection.
As part of Sygnia’s investigation into a separate threat actor, an account that was disabled by initial remediation efforts was re-enabled by a service account. Upon investigation, Sygnia determined that the account had been previously used by Weaver Ant. Notably, the activity originated from a server that had not been previously identified as compromised. This prompted a large-scale forensic investigation and as a result, Sygnia uncovered a variant of the China Chopper Web shell deployed on an internal server that had been compromised for several years.
“Nation-state threat actors like Weaver Ant are incredibly dangerous and persistent with the primary goal of infiltrating critical infrastructure and collecting as much information as they can before being discovered,” said Oren Biderman, Incident Response and Digital Forensic Team Leader at Sygnia. “Multiple layers of web shells concealed malicious payloads, allowing the threat actor to move laterally within the network and remain evasive until the final payload. These payloads and their ability to leverage never-seen-before web shells to evade detection speaks to Weaver Ant’s sophistication and stealthiness.”
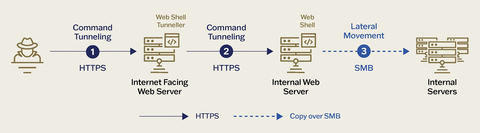
How Weaver Ant Tunneled into Telco
The web shell hunt revealed two types of web shells in different variants. The first was classified by Sygnia as an encrypted China Chopper. China Chopper enabled Weaver Ant to gain remote access and control of web servers. Notably, variants of the China Chopper web shell support AES encryption of a payload, making it highly effective at evading detection at the Web Application Firewall level.
The second web shell, INMemory was discovered by Sygnia and had no publicly available references to any other known web shells. INMemory’s leveraged just-in-time (JIT) compilation and execution of code at runtime to dynamically execute malicious payloads without having to write them onto the disk.
Biderman added, “Weaver Ant maintained activity within the compromised network for over four years despite repeated attempts to eliminate them from compromised systems. The threat actor adapted their TTPs to the evolving network environment, enabling continuous access to compromised systems and the collection of sensitive information.”
Following the investigation and an extensive eradication effort, Sygnia continues to monitor Weaver Ant. The threat actor has already been detected attempting to regain access to the telecom company’s network.
For the complete details, please see the associated report and technical annex.
About Sygnia
Sygnia is the world’s foremost cyber response and readiness expert. It applies creative approaches and bold solutions to each phase of an organization’s security journey, meeting them where they are to ensure cyber resilience. Sygnia is the trusted advisor and service provider of leading organizations worldwide, including Fortune 100 companies. Sygnia is a Temasek company, part of the ISTARI Collective. For more about Sygnia, visit Sygnia.co.
Contacts
Kathryn Thompson Dossey
Global Communications Manager
Media@sygnia.co
+1 704-776-8127